Future-proofing Your Interaction: Exploring the Most Current Telecom Solutions
Are you all set to future-proof your communication? In this short article, we will certainly discover the most recent telecommunications services that can reinvent the means you connect as well as attach. From the next development of 5G networks to the game-changing Internet of Things (IoT), we will explore exactly how these modern technologies can improve your interaction framework. Furthermore, we will go over just how cloud interaction and also fabricated knowledge are making it possible for performance, adaptability, as well as scalability. We will discover the relevance of cybersecurity in guarding your information as well as personal privacy. Prepare yourself to uncover the future of interaction!
5G Networks: The Following Development in Telecommunication

Among the vital benefits of G Networks is their rate. With download rates of as much as 10 gigabits per second, you can stream high-definition videos, play on the internet games with no lag, and download huge documents in seconds. Whether you are a trainee, a remote worker, or a gaming fanatic, G Networks can satisfy all your requirements.
G Networks offer unrivaled integrity. G Networks make sure that you remain attached at all times, even in jampacked areas or throughout top use hours.
In enhancement to speed up as well as reliability, G Networks likewise offer boosted safety features. With innovative file encryption protocols as well as robust firewall softwares, your information stays safe and secure as well as safeguarded from cyber hazards. You can browse the net, transfer sensitive info, and also perform online deals with tranquility of mind.
With their faster rates, reliable connections, as well as improved safety, you can remain ahead of the curve as well as take pleasure in a smooth interaction experience. Update to G Networks today and embrace the future of telecommunication.
Net of Points (IoT): Transforming Communication Facilities
With IoT, your interaction facilities is revolutionized. You can currently attach and also connect with a large range of sensing units as well as gadgets, making your day-to-day life extra reliable as well as practical. Imagine being able to regulate your residence devices, protection systems, as well as also your car, all from your smartphone or computer system. IoT allows this level of connectivity and automation, allowing you to stay linked and also in control no issue where you home are.
Among the crucial advantages of IoT is its ability to improve and maximize processes productivity. For organizations, IoT can supply important understandings and information that can be made use of to streamline procedures, decrease costs, as well as enhance consumer experiences. In production, IoT sensors can check devices efficiency, spot mistakes, as well as timetable maintenance instantly, minimizing downtime and making best use of performance.
IoT likewise has substantial implications for healthcare. With wise wearable devices as well as remote surveillance systems, medical care professionals can remotely track clients' crucial indicators, spot any type Bonuses of problems, and also give prompt treatments. This not only improves individual treatment yet additionally lowers the demand for constant medical facility visits, conserving time as well as resources.
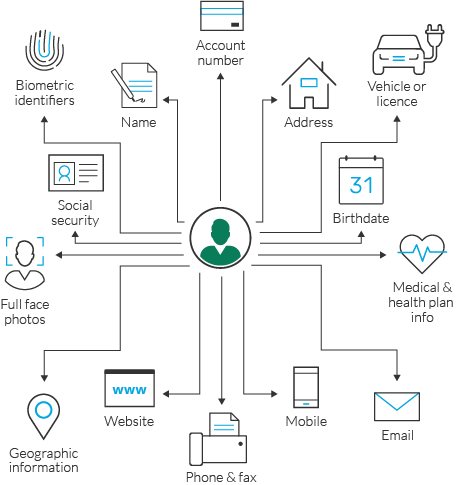
With the increased connectivity and also information exchange, safety comes to be a critical problem. It is important to apply durable safety procedures to safeguard your IoT tools and also the delicate data they generate. Security, verification, as well as regular software updates are just several of the procedures that can assist safeguard your interaction facilities.
Cloud Communication: Enabling Scalability and Adaptability
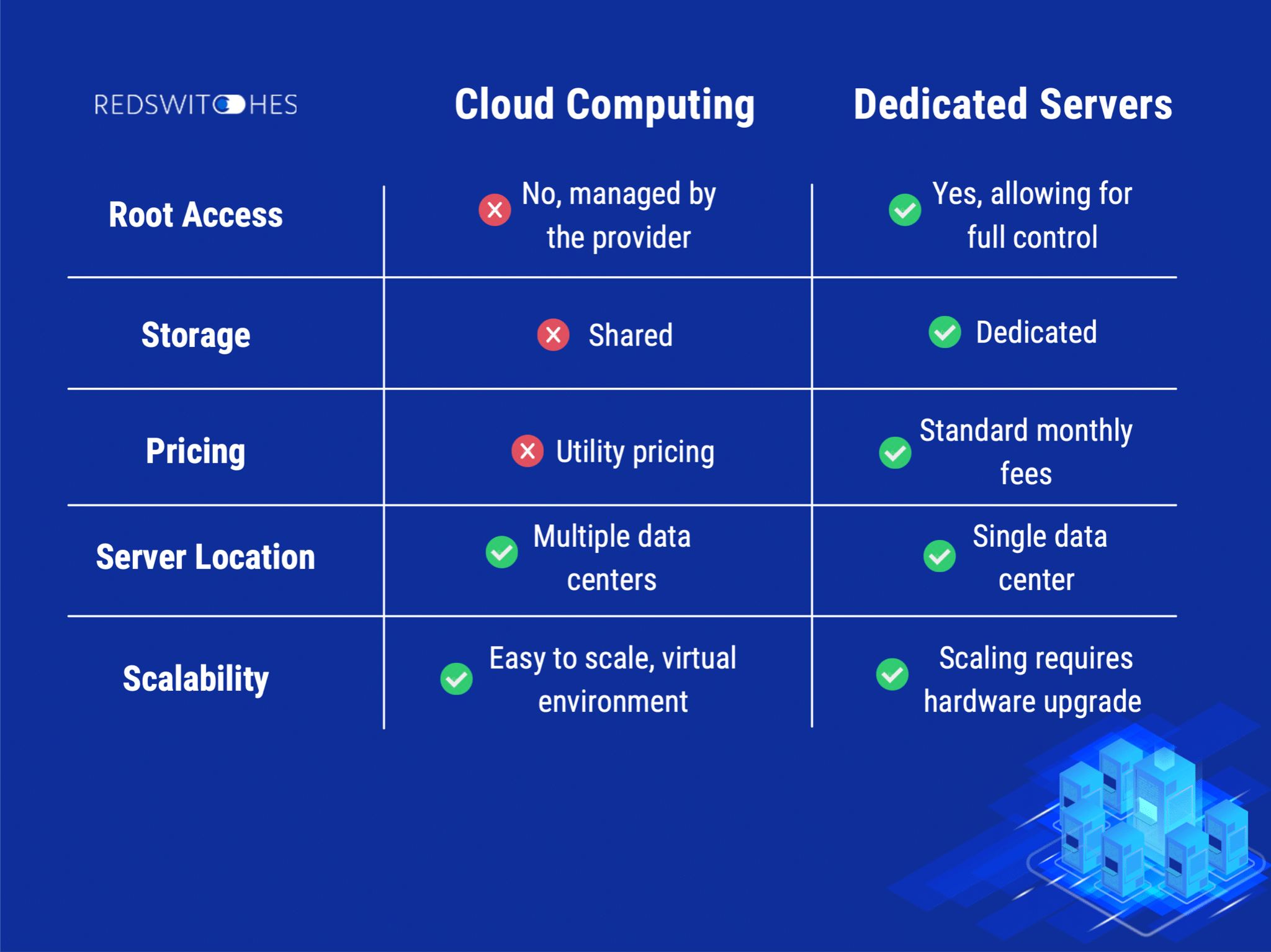
Cloud communication enables you to range and adjust your communication infrastructure easily. With typical communication systems, expanding your facilities to accommodate raising demands can be a facility and time-consuming procedure. By leveraging cloud-based interaction solutions, you can easily scale your resources up or down as required.
By utilizing cloud interaction services, you have the versatility to include or eliminate customers, phone lines, and attributes without the demand for physical facilities upgrades - Dedicated servers. This scalability permits your communication system to grow with your organization, guaranteeing that you can fulfill the developing needs of your employees as helpful hints well as consumers
In addition, cloud interaction gives real-time accessibility to sophisticated functions and functionalities that can enhance your communication capabilities. Whether it's call directing, call recording, or automated attendants, these attributes can be quickly executed and customized to fit your details needs.
Artificial Knowledge in Telecom: Enhancing Interaction Performance
Fabricated knowledge in telecommunications is revolutionizing communication efficiency by maximizing and also automating procedures network efficiency. By utilizing AI in telecom, you can automate repeated tasks, such as network monitoring and troubleshooting, freeing up your time to focus on more strategic initiatives. AI can aid in maximizing network website traffic administration, making sure that your communication channels are always operating at their greatest capacity.
Cybersecurity in the Telecom Sector: Shielding Information as well as Privacy
To safeguard your data as well as privacy in the telecom sector, you need to prioritize cybersecurity steps and stay alert versus prospective dangers. With the increasing reliance on digital communication, it is essential to safeguard sensitive information from unauthorized access and possible violations. By staying positive as well as informed, you can considerably decrease the risk of information breaches and protect your personal privacy in the telecommunications market.
Final thought
By exploring the most current telecom services, you have actually discovered just how to future-proof your communication. The Net of Things is changing communication infrastructure, allowing for smooth integration in between devices. Cloud communication supplies scalability and adaptability, while fabricated intelligence improves interaction efficiency.

Cloud communication enables you to scale and adapt your communication infrastructure easily. Synthetic intelligence in telecom is transforming communication effectiveness by automating procedures and also maximizing network performance. Cloud communication offers scalability and adaptability, while artificial knowledge boosts interaction effectiveness.